SAML2 authentication is a powerful tool for seamless Single Sign-On (SSO) integration. This guide explains how to configure a Moodle system as an Identity Provider (IDP) using the SimpleSAMLphp library and the Moodle SAML IDP plugin.
My Environment:
- Moodle version: 3.10
- PHP version: 7.2 (Use SimpleSAMLphp version 1.19 to match my moodle PHP version)
- SAML IDP Plugin: auth_samlidp
- SimpleSAMLphp Library & docuementation: SimpleSAMLphp version 1.19
Install the moodle SAML IDP Plugin
- Download the plugin from the Moodle Plugin Repository.
- Install the plugin through the Moodle front-end:
- Navigate to
Site administration > Plugins > Install plugins. - Upload the downloaded plugin ZIP file.
- Follow the installation process.
- Navigate to
Setting up SimpleSAMLphp
- Download and place SimpleSAMLphp:
- Download the SimpleSAMLphp 1.19 package.
- Place it under the directory
moodle/auth/samlidp, naming the foldersimplesamlphp.
- Configure the webserver (Apache) for SimpleSAMLphp access: Add the following configuration to the Apache virtual host or default site configuration:apache
Alias /simplesaml /var/www/html/moodle/auth/samlidp/simplesamlphp/www
<Directory /var/www/html/moodle/auth/samlidp/simplesamlphp/www>
Require all granted
</Directory> - Configure SimpleSAMLphp:
- Open the
config.phpfile insimplesamlphp/config/. - Edit the following values
- Open the
'certdir' => 'cert/',
'loggingdir' => 'log/',
'datadir' => 'data/',
'tempdir' => '/tmp/simplesaml',
'technicalcontact_name' => 'Administrator',
'technicalcontact_email' => '[email protected]',
'errorreporting' => true, // Set false in production
'showerrors' => true, // Set false in production
'module.enable' => [
'moodle' => true
],
'enable.saml20-idp' => true,
'store.type' => 'sql',
'store.sql.dsn' => 'mysql:dbname=<moodle_db_name>;host=<moodle_db_host>',
'store.sql.username' => '<moodle_db_user>',
'store.sql.password' => '<moodle_db_password>', -- we are storing session in to DB and expecting the SAME DB will be used for moodle
- Edit
authsources.php:- Add the following at the end of the file
'moodle-userpass' => [
'moodle:External',
'moodle_coderoot' => '<absolute_moodle_code_path>',
'logout_url' => '<moodle_url>/auth/samlidp/logout.php',
'login_url' => '<moodle_url>/login/index.php',
'cookie_name' => 'MoodleSAMLIDPSessionID',
], - Generate certificates:
- Navigate to the
simplesamlphp/cert/directory. - Run the following command to generate the certificates
- Navigate to the
openssl req -newkey rsa:3072 -new -x509 -days 3652 -nodes -out server.crt -keyout server.pemMove the server.crt and server.pem files to the simplesamlphp/cert/ directory.
- Edit metadata:
- IDP Metadata (
saml20-idp-hosted.php): - Confirm the following as we generated in above step
- IDP Metadata (
'privatekey' => 'server.pem',
'certificate' => 'server.crt',- SP Metadata (
saml20-sp-remote.php): Define metadata for the Service Provider (SP).
$metadata['https://sp.example.org/simplesaml/module.php/saml/sp/metadata.php/default-sp'] = [
'AssertionConsumerService' => 'https://sp.example.org/simplesaml/module.php/saml/sp/saml2-acs.php/default-sp',
'SingleLogoutService' => 'https://sp.example.org/simplesaml/module.php/saml/sp/saml2-logout.php/default-sp',
]; – key of $metadata [key] : this is entity id mentioned in SP metadata and rest are ACS url and Logout URL
- Copy Moodle plugin files to SimpleSAMLphp:
- Copy the
auth/samlidp/moodle/folder toauth/samlidp/simplesamlphp/modules/.
- Copy the
Verify the Setup
- Generate IDP metadata:
- Access the following URL:bashCopy code
<moodle-domain>/simplesaml/saml2/idp/metadata.php - Ensure the metadata includes correct endpoints and configurations.
- Access the following URL:bashCopy code
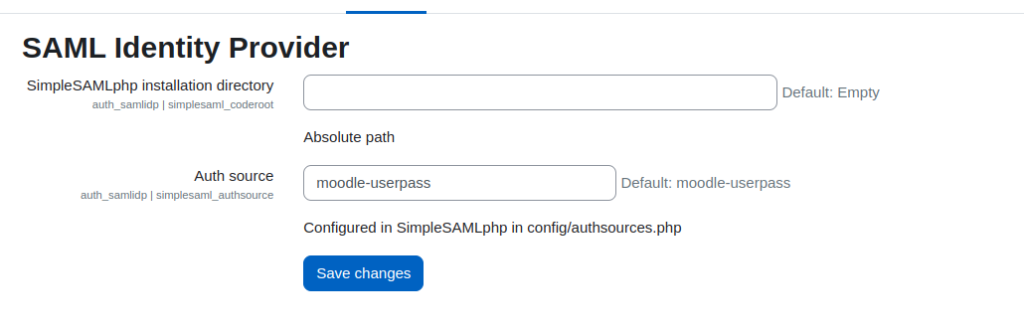
- Update the plugin settings in Moodle:
- Navigate to
Site administration > Plugins > Authentication > Manage authentication. - Configure the plugin with:
- Absolute path to the Moodle codebase.
moodle-userpassas the authentication source (can be changed as needed).
- Navigate to