OCI IAM and Policy
IAM
- Resource : Resources include compute instances, block storage volumes, virtual cloud networks (VCNs), subnets, and route tables etc
- User : use your company’s OCI resources
- Group : collection of users who all need the same type of access to a particular set of resources or compartment
- Compartment : A collection of related resources. A logical entity, available in tenancy across region for organizing and isolating your cloud resources for measuring usage and billing, access (by using policies)
- Tenancy: The root compartment that contains all your organization’s OCI resources
- Policy: A document that specifies who can access which resources and how. Access is granted at the group level and compartment level.
- Dynamic Gorup : When you use instance principals, you create dynamic groups. Dynamic groups allow you to group compute instances as principal actors, like user groups. You can then create policies to permit instances to make API calls against OCI services.
- Network Source : A group of IP addresses that are allowed to access resources in your tenancy. The IP addresses can be public IP addresses or IP addresses from a VCN within your tenancy.
- Each resource belongs to a compartment, by default, there is root compartment. The resource can belong to a single compartment, however, can be shared among compartments for usage and can be moved from one compartment to other.
- Can’t setup MFA for all, it is only 1/1 with MFA code, however, you can disable
- Credential Management
- Console password: login on browser console
- Secret key : For using the Amazon S3 Compatibility API with Object Storage
- Api Signing Key (pem file) : For API call
- Auth-token : for third party api authentication
- SMTP password : for OCI mail service
- DB password : For database system
- Swift Password : For using a Swift client with Recovery Manager (RMAN) to back up an Oracle Database system (DB system) database to Object Storage
- One user can generate two auth token, that does not expire and can be used for with third party api authentication
- IDP mapping
Policy
- Policies are under compartment, default root compartment
- Least privileged principal, even suggested that tenancy admin should not perform any operation except creation for group and policy
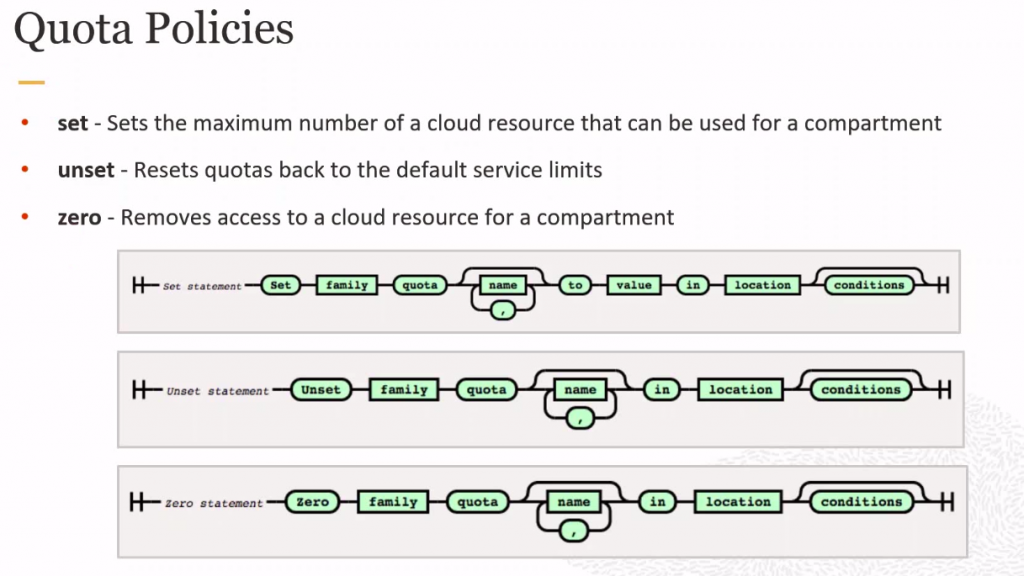
- Policy Construct : Allow subject [any-user/group/service/dynamicgroup/networkresource] to action [manage/use/inspect/read] [aggregate resource type/ individual resource type] in placement [account/tenancy/compartment] where condition [any|all {][request(permission/operation)]/target =|!= ‘’ ][}]
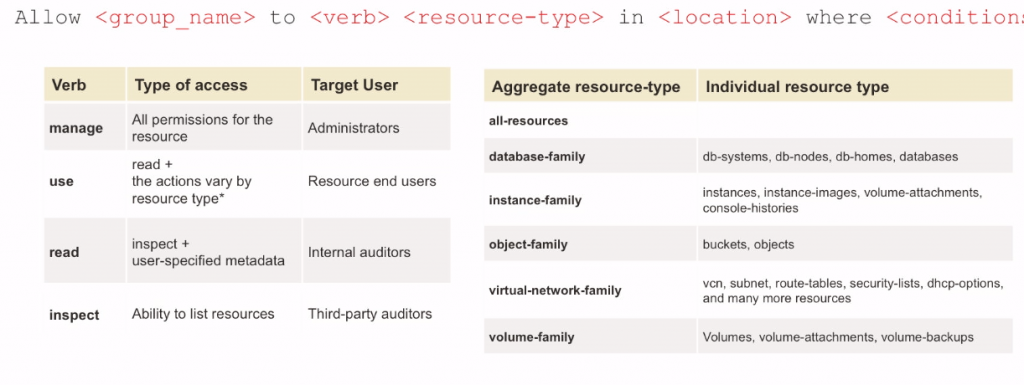
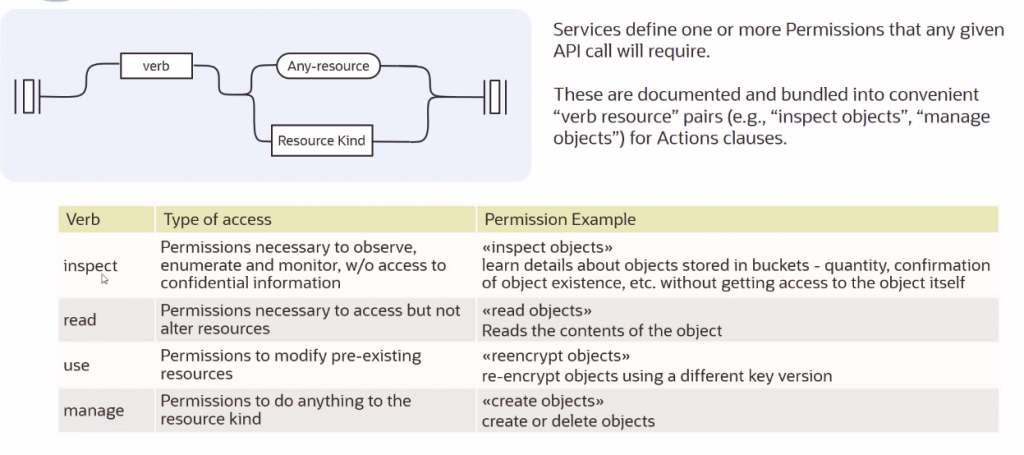
Common Policy : https://docs.oracle.com/en-us/iaas/Content/Identity/Concepts/commonpolicies.htm
Quota Policy
- To set limit of resources at compartment level.